Streaming TV while traveling the world
I travel the world frequently, spending months at a time away from home. I love to experience local food and culture when I travel. I also love my American sports and TV shows which are not available outside the US. Back in the day, a good VPN would solve the problem. But today, the VPN solution no longer works for most streaming providers that I use. So, I came up with a new way to allow myself access to all the streaming services while traveling anywhere in the world, except maybe China.
The idea is simple… make it look like the traffic to and from the streaming service is coming from your home network and home location. Easy right? There are many ways to accomplish this, but here is how I do it…
Step 1: A home proxy
My traffic looks like it is coming to and from my home, because it actually is. I setup a proxy server on my home network that brokers all the traffic between me, wherever I am, and any streaming service I use. I connect to the proxy server via ssh and setup a dynamic port forwarding tunnel. To accomplish this, you’ll need a proxy server. A raspberryPi will work, or any spare computer with enough bandwidth and processor to make it work. Run an ssh server on the proxy server. Be sure to enable ssh tunneling in the /etc/ssh/sshd_config file… PermitTunnel yes.
Create a user account on the proxy server and put your ssh public key in the ~/.ssh/authorized_keys file so you can login without a password.
Step 2: Port forwarding
Now that you have a proxy server running sshd on your home network, you need to expose it to the internet. Do this by configuring port forwarding on your home internet router. Don’t expose port 22! I’ve found that some internet providers block incoming traffic on lower ports. Choose some random port number to expose and forward that traffic to port 22 on your proxy server. Let’s choose port 9876 for now.
With port forwarding setup, you should now be able to access your proxy server from anywhere with the command ssh -p 9876 <user>@<my-public-ip>. Try it from your friend’s house or a local coffee shop.
But we’re not done yet…
Step 3: Dynamic DNS
Because your home IP address can change without notice, you’ll want to use dynamic DNS to be able to access the home proxy server by name rather than IP address. To accomplish this setup a dynamic DNS service. I use https://freedns.afraid.org/ because it’s free! Setup an account, pick a free domain, add your A record to one of their free domains. Get the wget or curl command so you can make a crontab on your proxy server. My crontab on my proxy server looks something like this…
@hourly /usr/local/bin/wget -q --read-timeout=0.0 --waitretry=5 --tries=400 http://freedns.afraid.org/dynamic/update.php?<secret> -O /dev/null
This ensures that any change to my IP adress will be reflected in my DNS hostame within an hour. With dynamic DNS setup you can now access your proxy server from anywhere with the command ssh -p 9876 <user>@<hostname>. Progress! And again, test this from your friend’s house or a local coffee shop.
Step 4: Connect and tunnel traffic
While at home, you can visit https://whatismyipaddress.com/ to see your IP address. While you are away, you want this website to tell you that your IP address is the same one you see there when you are at home. Now that you have the proxy server setup with an ssh server, exposed it to the internet, given it a hostname via dynamic DNS, you are ready to connect and tunnel traffic. Before you leave for Mexico, go over to your friend’s house and see if it works. Connect to your home proxy server with the following command… ssh -D 1337 -p 9876 <user>@<hostname>. This ssh command configures dynamic port forwarding on localhost port 1337. The tunnel is ready! Next, open your computer proxy settings and and configure a SOCKS proxy at localhost:1337.
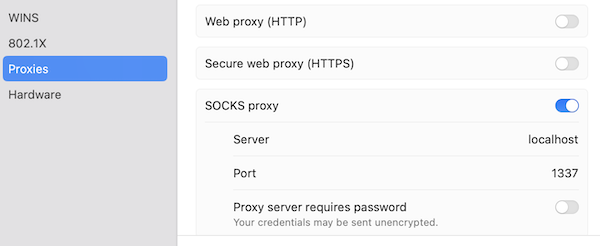 If all is working as expected you should see your home IP address when you visit
If all is working as expected you should see your home IP address when you visit https://whatismyipaddress.com/.
Step 5: Fake your location
There are two ways a streaming service can know if you are not at home. 1) your IP address, and 2) your location reported by the browser. The IP address is sorted, see above. For the location reported by the browser, I use a browser plugin called Location Guard. Configure this plugin to report the fixed location of your home.
Conclusion
This method is bulletproof. With my traffic now proxying through my home network and my browser reporting my location as my actual home location, I am able to stream all content from every streaming provider I have, including Hulu, Netflix, Peacock, AppleTV, Amazon Prime Video, HBO Max, Disney+ and more. It looks like the traffic is coming to and from my home because it IS coming to and from my home via the home proxy server. I have also configured my browser not to rat me out. Boom!
Tips
- Use a seperate browser, or browser profile, for streaming that is configured with Location Guard permanently.
- Make an alias to connect to the proxy server and configure your local proxy settings, and one to unconfigure your local proxy settings also. Here are mine…
alias proxy='networksetup -setsocksfirewallproxy "Wi-Fi" localhost 1337 ; ssh -D 1337 -p 9876 <user>@<hostname>' alias poff='networksetup -setsocksfirewallproxystate "Wi-Fi" off'